In today's digital age, smartphones have become an integral part of our daily lives. From managing personal information to conducting business transactions, these devices hold a wealth of sensitive data. However, with the rise in cyber threats, it's crucial to be aware of potential hacking risks. Understanding the subtle signs that your device might be compromised is the first step towards safeguarding your personal and professional information.
Identifying if your phone has been hacked can be challenging, especially when hackers use sophisticated techniques to remain undetected. This article delves into ten subtle signs that may indicate your device has been compromised and provides practical steps you can take to protect yourself. By staying informed and proactive, you can significantly reduce the risk of falling victim to cybercrime.
Stay on the lookout for the signs below: Your device is slowing down, heating up, or draining the battery. These are some of the most common indicators that something might be amiss with your smartphone. If your phone overheats, slows down, drains the battery too fast, or if your phone bill seems unusually high, it could be a sign that unauthorized access has occurred. Let’s explore these warning signs further and understand what they mean.
Recognizing Performance Issues
One of the primary signs that your phone might be hacked is a noticeable decline in performance. If your device starts lagging, taking longer to load apps, or freezing frequently, it could be due to malicious software running in the background. Such software often consumes significant system resources, leading to sluggish performance.
Besides performance issues, another red flag is excessive heat generation. If your phone becomes unusually hot even when not in heavy use, it might indicate that unauthorized processes are consuming power. Overheating can also lead to hardware damage over time, making it essential to address this issue promptly.
Additionally, rapid battery drainage is a telltale sign of potential hacking. Malware often runs continuously in the background, draining your battery faster than usual. Monitoring your battery usage patterns can help identify any unusual activity that might suggest a breach.
Unusual Data Consumption Patterns
Another subtle indicator of phone hacking is unexpected spikes in data usage. If you notice a sudden increase in your mobile data consumption without any apparent reason, it could mean that someone is using your device to send or receive large amounts of data. This could involve downloading harmful files or transmitting sensitive information from your phone.
Data usage anomalies can also point to unauthorized access through apps that have been compromised. Hackers often exploit vulnerabilities in third-party applications to gain entry into your device. Regularly reviewing your data usage details can help detect such irregularities early.
Furthermore, keep an eye on your monthly bills. A higher-than-normal bill might signify that your phone is being used for activities beyond your control. Unexplained charges should raise suspicion and prompt immediate investigation into possible security breaches.
Security Measures Against Hacking
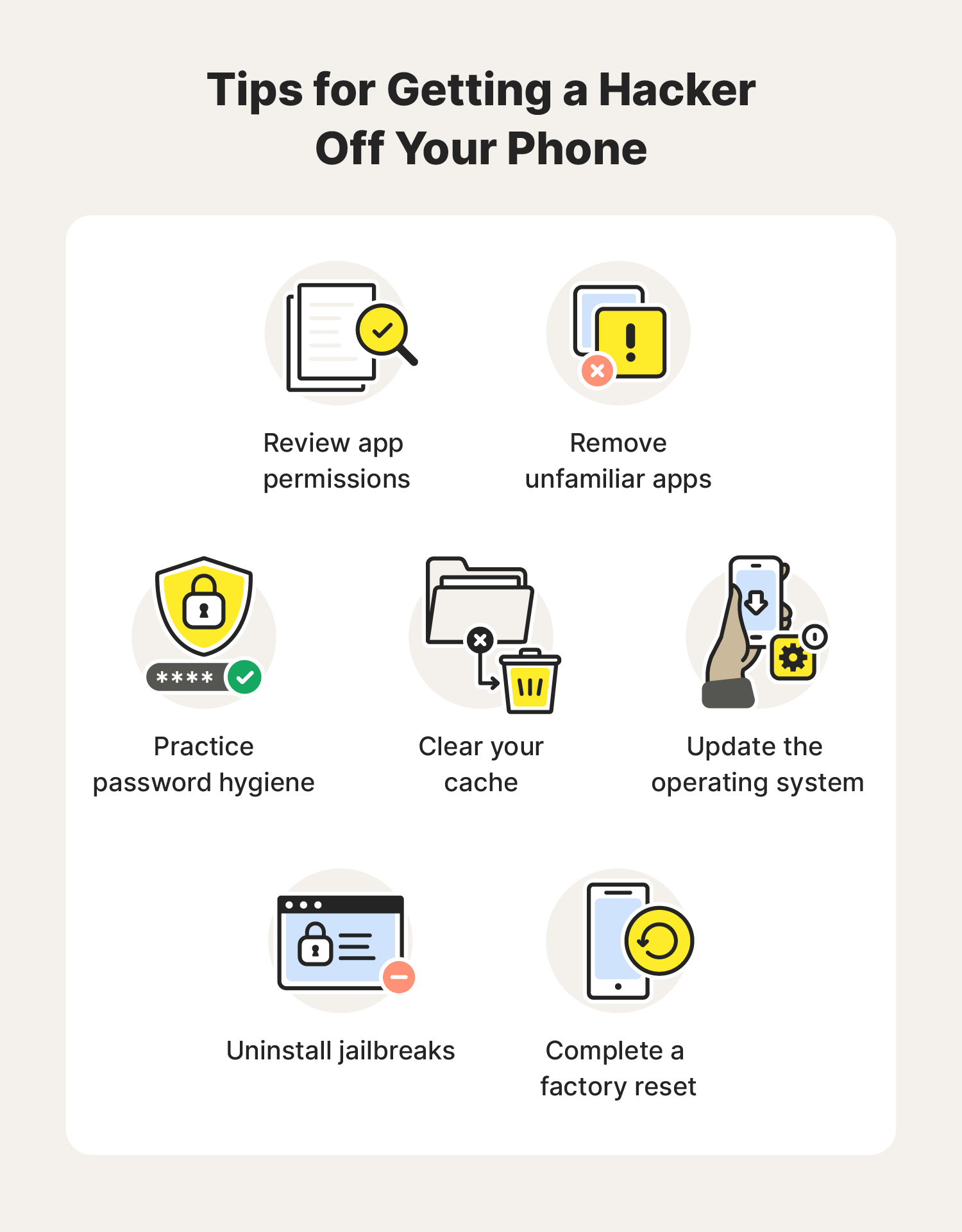
To protect your device from potential hacking attempts, consider implementing robust security measures. Start by enabling two-factor authentication wherever possible. This adds an extra layer of protection to your accounts, making it harder for hackers to gain access even if they obtain your password.
Regularly updating your operating system and apps is another critical step. Software updates often include patches for newly discovered vulnerabilities, ensuring that your device remains secure against emerging threats. Ignoring updates can leave your phone exposed to attacks exploiting outdated code.
Lastly, avoid sideloading apps unless absolutely necessary. While Android allows easier installation of apps from unknown sources, doing so increases the risk of downloading malicious software. Stick to trusted app stores like Google Play or Apple App Store to minimize this risk.